Last update images today How To Do Web Attacks Black Hat


























https cdn acunetix com wp content uploads 2012 10 web apps 3 jpg - Web Application Attack What Is It And How To Defend Against It Web Apps 3 https cdn brighttalk com ams california images communication san 504356 preview 1628782818 png - The August Cyber Lookback From Black Hat NOC Recap To Apple S Hashing Preview 1628782818
https d3f1iyfxxz8i1e cloudfront net courses course image 29f2449756fe jpg - Black Hat Talk Abusing Web APIs Through Scripted Android Applications 29f2449756fe https d3f1iyfxxz8i1e cloudfront net courses course image 0cd2ddcf118e jpg - Black Hat Talk Exploit Mitigation Improvements In Windows 8 From Black 0cd2ddcf118e http www exhibitionstand contractors Content media image 2023 11 3273 orig gif - BLACK HAT 2024 Saudi Arabia 3273 Orig
https blog barracuda com content dam barracuda blog images 2021 02 threat spotlight WAF WAFaas graph1 jpg - Threat Spotlight Automated Attacks On Web Applications Threat Spotlight WAF WAFaas Graph1 https blogger googleusercontent com img a AVvXsEgIVVEMl8r q foMvyELQSdr1kILW7reZsofnyHkhJpZ0BH0WJq4hnamJmtSs yOkNgBu4U6XlkcqBzUdey0u9uAckb19GNpz5qtOolBHd4qazioSE rGchx5Y85SvJ0vj7JgTFxJFN cWm UO7Kp8 3e 4EiOkcy0Vx FT7TCPk1OztGeiIUMY9 18iP7 - Hacker S Toolkit Black Hat Go Next Gen Security Tests 2024 AVvXsEgIVVEMl8r Q FoMvyELQSdr1kILW7reZsofnyHkhJpZ0BH0WJq4hnamJmtSs YOkNgBu4U6XlkcqBzUdey0u9uAckb19GNpz5qtOolBHd4qazioSE RGchx5Y85SvJ0vj7JgTFxJFN CWm UO7Kp8 3e 4EiOkcy0Vx FT7TCPk1OztGeiIUMY9 18iP7
https d3f1iyfxxz8i1e cloudfront net courses course image c836eb2c8466 jpg - Black Hat Talk Evasion And Detection Of Web Application Attacks From C836eb2c8466
https d3f1iyfxxz8i1e cloudfront net courses course image 29f2449756fe jpg - Black Hat Talk Abusing Web APIs Through Scripted Android Applications 29f2449756fe https cdn acunetix com wp content uploads 2012 10 web apps 3 jpg - Web Application Attack What Is It And How To Defend Against It Web Apps 3
https brightsec com wp content uploads 2023 05 8 Types of Web Application Attacks scaled jpg - 8 Types Of Web Application Attacks And Protecting Your Organization 8 Types Of Web Application Attacks Scaled https d3f1iyfxxz8i1e cloudfront net courses course image 0cd2ddcf118e jpg - Black Hat Talk Exploit Mitigation Improvements In Windows 8 From Black 0cd2ddcf118e
https d3f1iyfxxz8i1e cloudfront net courses course image ebead1a7ff19 jpg - Black Hat Talk Attacking Web Services Next Generation Of Vulnerable Ebead1a7ff19 https www eccouncil org cybersecurity exchange wp content uploads 2022 03 Web Application Attacks 1 1024x512 jpg - How To Defend Against Common Web Application Attacks EC Council Web Application Attacks 1 1024x512 https i pinimg com 736x 43 b3 f0 43b3f0e4d22c856ec223ca2b28bc0384 jpg - 5 Unveiling The Dark Secrets Of Black Hat Hackers How They Re Stealing 43b3f0e4d22c856ec223ca2b28bc0384
https cdn brighttalk com ams california images communication san 504356 preview 1628782818 png - The August Cyber Lookback From Black Hat NOC Recap To Apple S Hashing Preview 1628782818 https i ytimg com vi iblaclWrpRA maxresdefault jpg - Top 5 Web Application Attacks In 2024 YouTube Maxresdefault
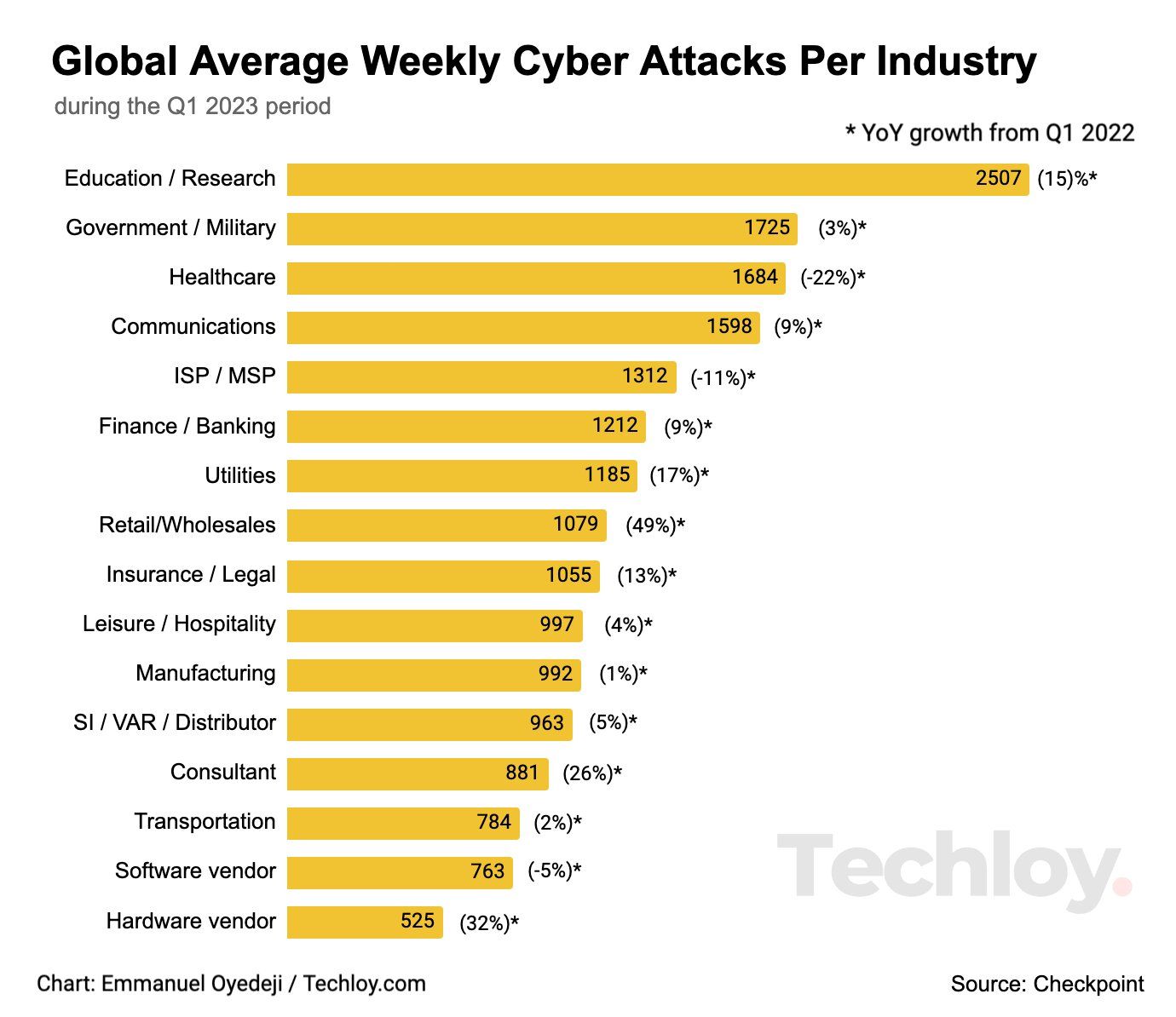
https www techloy com content images 2023 05 Global Average Weekly Cyber Attacks Per Industry jpeg - CHART Cyberattacks Rose Globally In Q1 2023 Driven By The Global Average Weekly Cyber Attacks Per Industry
https i ytimg com vi iblaclWrpRA maxresdefault jpg - Top 5 Web Application Attacks In 2024 YouTube Maxresdefault https img playbuzz com image upload ar 1 5 c pad f jpg b auto cdn 3ebc9c65 6861 4fe6 8dae 2f296511ee1b d02edc38 e8cb 4640 abc1 833428440e9a jpg - Black Hats White Hacks And The Dark Web A Quick Guide Through Cyberspace D02edc38 E8cb 4640 Abc1 833428440e9a
https i pinimg com 736x 43 b3 f0 43b3f0e4d22c856ec223ca2b28bc0384 jpg - 5 Unveiling The Dark Secrets Of Black Hat Hackers How They Re Stealing 43b3f0e4d22c856ec223ca2b28bc0384 https base binus ac id wp content uploads 2024 02 CyberAttack2024 gif - 8 Serangan Siber Tertinggi 2024 BINUS School Of Engineering CyberAttack2024
https d3f1iyfxxz8i1e cloudfront net courses course image 29f2449756fe jpg - Black Hat Talk Abusing Web APIs Through Scripted Android Applications 29f2449756fe https d3f1iyfxxz8i1e cloudfront net courses course image c836eb2c8466 jpg - Black Hat Talk Evasion And Detection Of Web Application Attacks From C836eb2c8466 https img playbuzz com image upload ar 1 5 c pad f jpg b auto cdn 3ebc9c65 6861 4fe6 8dae 2f296511ee1b d02edc38 e8cb 4640 abc1 833428440e9a jpg - Black Hats White Hacks And The Dark Web A Quick Guide Through Cyberspace D02edc38 E8cb 4640 Abc1 833428440e9a
https findbestcourses com wp content uploads 2023 02 types of cyberattacks feat 1 jpg - Cyber Security Attacks And It S Type Types Of Cyberattacks Feat 1 https www carriermanagement com assets bigstock hacker at computer data reflected eyeglasses 375685612 jpg - Haute Cyber Attackers Are Strutting Into 2024 With More Sophistication Bigstock Hacker At Computer Data Reflected Eyeglasses 375685612
https wiki kaduu ch doku lib exe fetch php - Dark Web Monitoring Kaduu CTI 2024 Fetch.php